What is a VPN and what is it for?
Unless you’ve been hiding under a rock for the past couple of decades, you’ve most likely heard of a VPN. They’ve become widely popular for those who care about their privacy while browsing the web, and have even made headlines in the news.
But what exactly is a VPN, and how does it work? We’ll be explaining everything right here, as well as detailing the use case of one.
Fancy getting yourself a VPN? Then we recommend taking advantage of the latest deal from NordVPN, which is now available for £2.65 per month when the TrustedReviews code is applied at checkout. Nord is even throwing in three extra months on top of the 2-year plan at no extra charge.

Save 81% on a VPN with SurfShark
Surfshark has dropped the price of its VPN to £1.94 a month. Head over to Surfshark now to pay a one time price of £46.44 for 24 months of Surfshark and save 81%.
- Surfshark
- 81% off
- £1.94 a month
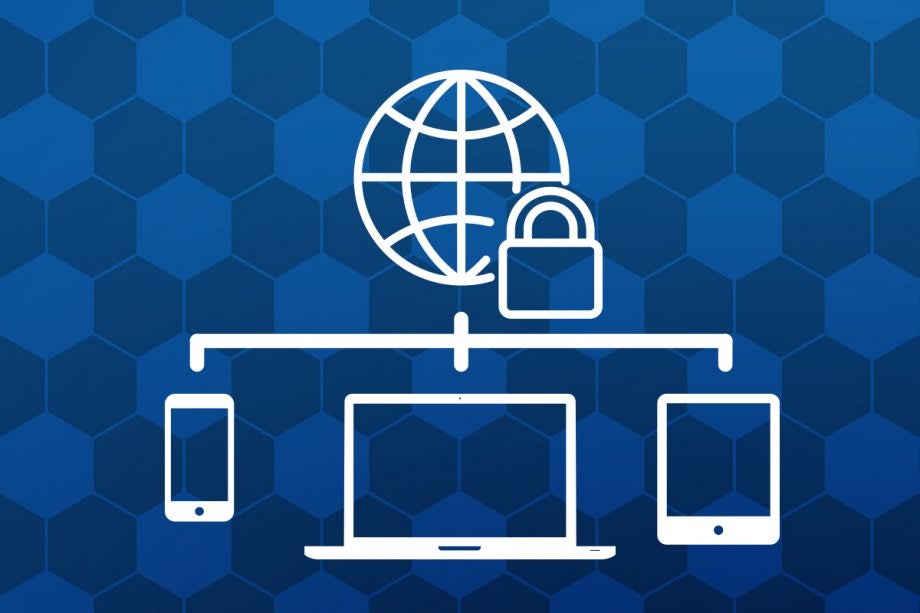
What is a VPN?
A VPN (virtual private network) is used to establish a secure connection to the internet via an encrypted tunnel to a remote server. Doing so will hide your IP address, so third parties are unable to determine your location, identity or browsing history.
This process will also improve the security of your connection, reducing the likelihood of a hacker stealing your data, especially on a public Wi-Fi network.
VPNs allow you to connect to servers across the globe, with NordVPN currently offering servers in 60 different countries. By using a foreign server, you will be able to visit websites that only allow access for users in a specific country. For example, you’d be able to access iPlayer from outside of the UK.
But while VPNs are perfectly legal to use, you could be breaking the terms and conditions of streaming sites such as Netflix by using a VPN to access geo-restricted content. As a result, many streaming services will try to block your access if it detects that you’re using a VPN.
There are plenty of other legitimate use cases for a VPN. Many online retailers, especially airlines, will hike up prices if you’ve visited a page multiple times in a short space of time. But using a VPN will make it difficult for a retailer to track your browsing history, therefore ensuring the prices remain the same.
There are drawbacks to using a VPN though, as it can slow down the speed of your internet connection. And while there are free VPNs available, they will usually have a limited number of servers or bandwidth per month, so you’ll generally have to pay a monthly fee for the best experience.
What types of VPN are there?
The most common VPN you’ll read about, and what we have focused on most in this guide, is a personal VPN. This is used by an individual to maximise their privacy while browsing the web.
Then you also have a site-to-site VPN, which is typically reserved for businesses. This allows two separate teams or more (typically in different locations) to access each other’s networks securely, so they can share sensitive information without fear of it being snooped on by third parties.
And finally there’s a remote access VPN, which allows you to connect to a remote private network. This is most commonly used by remote workers, who need to access their office’s security-tight network from a different location. Again, this is useful for any business that handles private data and sensitive information.