The Samsung Galaxy S10’s fingerprint sensor has been fooled by a 3D printed model

Most smartphone security is now hinged around just one metric: your fingerprint. Your one-of-a-kind print is used to secure all manner of things, from phone payment, banking apps, password managers and even messaging services like Telegram. So, what would happen if someone could trick your phone with a 3D-printed copy of your digit?
One post on Imgur, by user Darkshark, shows a user fooling the in-display reader on Samsung Galaxy S10 with a 3D printed copy of his own fingerprint. The methodology veers strongly towards Spysville, with the amateur James Bond doing it all with nothing more than a smartphone, a PC and a 3D printer.
Related: Best VPN 2019
But how did he do it? Darkshark first took a photo of his own fingerprint on a wineglass with a smartphone. Then, he processed the image in photoshop and made a model in 3ds Max that allowed him to print out a model of his fingerprint. It took Darkshark a few attempts to get the height correct, but on his third attempt he cracked it and was able to print a version of his fingerprint that would unlock the phone after just a 13-minute print.
Darkshark then suggests how he could use this in the real world: “If I steal someone’s phone, their fingerprints are already on it,” said Darkshark. “I can do this entire process in less than 3 minutes and remotely start the 3d print so that it’s done by the time I get to it. Most banking apps only require fingerprint authentication so I could have all of your info and spend your money in less than 15 minutes if your phone is secured by fingerprint alone.”
Related: Best iPhone 2019
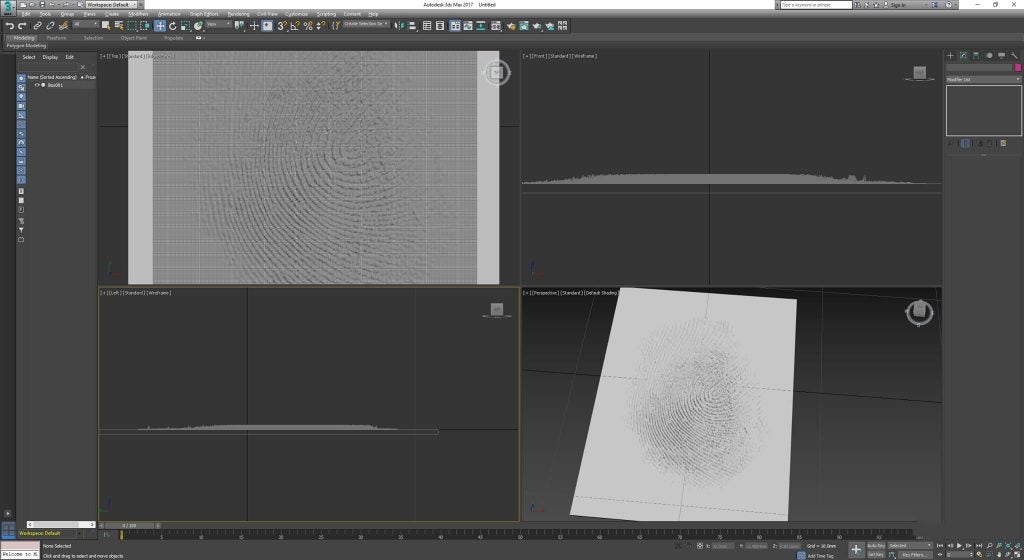
Taken from Darkshark’s Imgur post.
It’s unfortunate news for owners of the Samsung Galaxy S10. The fingerprint scanner is supposed to be using a more secure ultrasonic scanner that is harder to fool. However, it seems with just a few bits of technology and a quarter of an hour, this can be tricked too.
This story isn’t unique, with several other biometric security measures being fooled by security researchers — and in some cases even the police — over the years. It does show that there’s still a little way to go before we can fully secure our phones. Especially now that Darkshark has carefully explained his methodology, so anyone with access to a 3D printer could feasibly have a crack.
What do you make of this security SNAFU? Let us know on Twitter at @TrustedReviews


