Twitter’s password fail shows that we deserve better security.

Just recently, Twitter was hit by hackers who managed to get hold of some user data including ‘hashed’ passwords for a few hundred thousand users. It was possible for hackers to run password cracking programs to compare millions of dictionary words and alternate spellings to the hashed password list to see if any matched.
To Twitter’s credit everyone was contacted quickly and a blanket password reset was put in place for anyone affected, forcing users to set new passwords in case the hackers managed to work out what their passwords were. Although on the one hand this demonstrated Twitter’s proactive approach to security problems, it also shows a key vulnerability in how we protect our private data – the password.
We rely on passwords all day, every day. From our iTunes account to web mail to the PC network at work we use username and passwords combinations to keep our digital lives under control. I say digital lives, but there is increasingly only the thinnest of membranes between those and our actual, ‘real’ lives. If someone was to find a notebook with all of your passwords scribbled in its pages, they could destroy your finances, your job and much of your social life before you could say Mother’s Maiden Name.
It is over fifty years since the first computer password system was created and around forty since the method of ‘hashing’ passwords to keep them secure was first implemented. Unfortunately, the technology has not moved on a great deal from there.
The problem with passwords, as any long suffering IT helpdesk drone will tell you from the bottom of their glass, is that they are either too easy to guess or too secure to remember. The standard advice for creating a password goes like this:
- don’t use real words
- don’t use personal information (mum’s maiden name, name of your first pet) as it can be guessed or discovered.
- use numbers and non-alphanumeric character where possible
It is all good advice on the face of it, but really they are just three ways of saying ‘make your password so difficult to remember you have to write it down on a Post-It and stick it on the bezel of your monitor’, which is a shame as the fourth piece of advice is invariably
- never write your password down, particularly on a Post-It stuck on the bezel of your monitor
Another wrinkle to the password problem is that ‘easy to guess’ doesn’t mean guessable by a person. Most password systems work using a one-way algorithm. You run a password through it and it creates a ‘hash’ – a garbled-looking jumble of characters. Only your password would create that hash by passing through the algorithm, but you can’t use the hash to figure out what the password is. It’s a one-way street.

One way for a hacker to approach this problem is something called a ‘dictionary attack’. They get hold of the file of hashed passwords (often stored relatively in the open due to the way the login code needs to access them) and use software to run thousands of words through the algorithm until they find one that matches one of the hashes. The speed of modern processors means it is possible to run through several complete dictionaries in multiple languages, plus misspellings and ‘clever’ obfuscations like swapping ‘e’ for ‘3’ in a relatively short time.
All Eyeballs and Fingertips
If passwords are so inherently flawed, why do we use them? There have been many proposed replacements for the password in the last fifty years. Biometrics seem like a promising avenue – if the problem lies in identifying a person then surely unique attributes such as fingerprints, a person’s iris patterns or even their DNA might be better than a secret keyword. One recent idea involves the use of a person’s heartbeat to generate a unique pattern.
Unfortunately, biometrics have a serious flaw – they rely on the fact that they cannot be reproduced. If someone was to work out a way to copy your unique attributes then the game is up. Indeed, this has been shown to be possible. You can fake a fingerprint with an imprint in gelatine taken from a latent print on a glass. In the extreme case, you could always cut off the required body part to waggle in front of a sensor.
Worse, once your biometrics have been compromised, they are impossible to change. You can think of a new password, but thinking of a new finger will get you nowhere.
Other schemes involves using CAPTCHAs to encrypt a difficult password with an easy one or even analysing your behaviour from voiceprint to gait recognition (the rhythm of your walk) to prove that you are who you say you are. Unfortunately, these are either overly complicated or unproven. They could be not only crackable, but easily so.
Key fobs or ID cards are another option, but these can be lost or stolen and having them fall into the hands of a thief could be catastrophic.
There is a quote attributed to Winston Churchill that goes, “Democracy is the worst form of government, except for all those other forms that have been tried.” It’s the same with passwords. Imperfect, but the best at what they do. What is needed to something to make them better.
That something is Two-factor Authenticaton. When you log in with username and password, you are challenged with a code to which you must respond, using some software to generate the correct answer.
Google will already let you set this up for Gmail and will even do the challenge/response part for you and text you the correct answer to key in. If you prefer, you can use an app for Android or iOS to generate the unique answer instead.
This kind of challenge/response authentication is risky on its own – after all, you could have your phone stolen and be up the creek – but combined with the username/password combo it gives an extra layer of authentication. Crucially, one that is hard for a hacker running a dictionary attack from their basement to reproduce.
Google already offers this, although not by default*. Other sites should too. You might not think that you need two-factor authentication on a site like Twitter, but granting someone access to a fragment of your identity can have unexpected consequences. Someone impersonating you on one site can help them to socially engineer information from you or your friends that can get them access to other, more crucial data.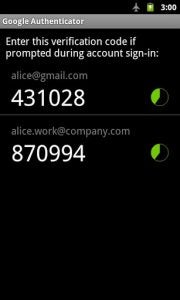
The only things stopping two-factor authentication from taking off are the expense of implementing it and user education about password vulnerabilities. The latter will sadly become more widespread as more sites are hacked and passwords reverse-engineered. The former should be something that we demand as customers. Perhaps not for every site but for email, e-commerce, dating sites and any social media we care about it should be an option. There are signs that Twitter is planning to step up and join Google in the fight for better login security, but what about Yahoo Mail, Facebook, Microsoft and all the other sites that we rely on?
The slightly Faustian bargain that we make with free web services is this – you give us a useful service, we give you data about us to turn into money. In doing so, we trust sites to look after that data and it is time that more companies took this responsibility seriously.
Have you ever been hacked? Let us know your experiences in the comments.
(* you need to delve into your account settings and we recommend that you do.)


