TrustWare BufferZone Pro Review
TrustWare BufferZone Pro
The next step in protecting your PC.

Verdict
Any of you that use PCs everyday should be all too familiar with the constant battle to keep at bay all the latest viruses, Trojans, and all the other nasty bits of software – collectively known as malware – that attack our workhorses. The daily deluge of updates and security warnings combined with the all conquering knowledge that the battle to rid your PC of these threats will never truly be won is enough to depress even the most chipper among us.
Of course, it didn’t always use to be like this. Back in the day, as long as you kept your computer protected from wayward floppy disks, you were sitting pretty. The real problems came with the arrival of the Internet and since then attacks on our PCs have simple skyrocketed. From the lowly “click on me” virus attachments in emails, to the most aggressive of Trojans that sneak in through an unpatched hole in your operating system, they come at you from all angles and, to keep them all at bay, the list of programs you need to protect everything has also mushroomed.
Nowadays it’s not uncommon to have anti-virus and anti-spyware software, a decent firewall (either hardware or software), spam filters, and a browser that detects phishing websites. So, bearing in mind the already considerable space and processing power of all these programs, there’s probably two ways you will view the arrival of Trustware’s Bufferzone software. The first is with a skeptical mindset that thinks ‘I’ve got enough anti-thisthatandtheother progams to worry about already, why would I want another one’ or the alternative is to look at it more positively, that is ‘you can never have enough protection, so gimme, gimme, gimme!’ 
Before I get too caught up in the semantics, though, let’s take a look at what Bufferzone actually does and then we’ll see if it’s worth recommending, regardless of which of the above reactions you had.
First things first, BufferZone is Windows XP only so, unless you’ve doggedly stuck with XP on your home machine, or you’re in control of one of the vast majority of corporate networks that still use XP, you may want to stop reading now. However, knowing that a Vista version is in the works – no release schedule as yet – you might also like to read on to find out what could be coming your way.
BufferZone, then takes a whole new approach to protecting your computer. Rather than using the retroactive method employed by most anti-virus software, where malicious software has to be manually identified then added to the anti-virus software’s threat list by means of an update, BufferZone proactively protects your PC by hiding the real operating system behind a wall and ensuring all untrusted software is kept safely on the other side.
This protective wall is created by a process called virtualisation, whereby one piece of software running on your actual PC creates a software environment that acts like it is your actual PC – it creates a virtual PC or buffer zone. The trick being, the software running inside this virtual PC is completely isolated from your actual PC so if it tries to do something untoward it doesn’t actually harm your real PC. All that’s required to get rid of the harmful software is to delete the Virtual PC and start again.
Now, virtualisation software has been around for a while and there are plenty of solutions that enable you to run software in this way. However, none have ever been quite as easy to use as this one. Setting up BufferZone is as simple as running an installer and rebooting your PC. That’s it, you’re protected.
By default, the BufferZone protects Internet Explorer, Windows Media Player, and MSN Messenger so anything that is downloaded through these programs is kept in this pseudo quarantine. What’s more, any script or hack that exploits security holes in these programs is also blocked by the invisible wall of the virtual PC. 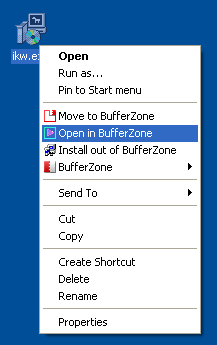
You can also assign any other program to be run in the BufferZone, like your preferred web browser, peer-to-peer applications, IRC client, and email clients (in the case of email clients, the client itself isn’t run in the BufferZone but any attachments or other saved files are). There’s also an option to run all software from other locations – like CD-ROMS and USB drives – in the BufferZone. So, baring a direct attack on your operating system, your computer has the potential to be totally safe.
The best part, though, is that as well as allowing programs to be run in the buffer zone, entire programs can also be installed there. So, if you want test a piece of software that you think might be dodgy, you can download it and install it (registry keys and all) within the BufferZone and see if anything bad happens. If all is well you simply uninstall it from the BufferZone, move the installer to the safe zone and install it again.
The icons and windows of programs, files, and folders in the BufferZone are encircled by a red line, so you always know if you’re working in a secure or unsecure environment. However, if you find this distracting you can disable it in the configuration menu.
We started testing the effectiveness of all this protection by downloading and installing programs deemed to be infected by our conventional virus scanners and we were glad to see our PC remained completely uninfected. Depending on what the malware was we saw the odd error message as the virus or Trojan obviously fell over trying to get passed the BufferZone. However, a quick empty of the BufferZone later and we had a completely clean machine again.
We then tried various combinations of running and installing programs from within and without the BufferZone, to see if they operated correctly. And in all the programs we tried, not one came a cropper. The one oddity we did notice was that, due to the way BufferZone actually stores programs in its virtual machine, links in certain menus, namely the quick launch section at the top of the start menu, could become broken. However, normal shortcuts operated as expected. 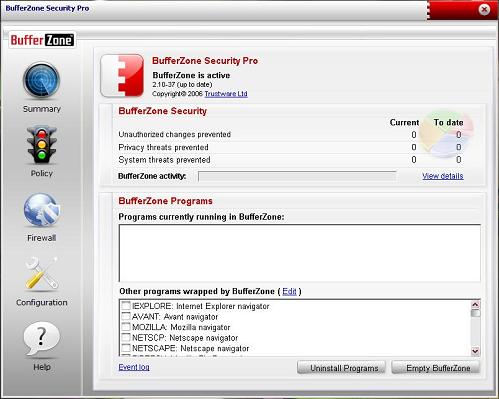
Overall, the experience of using BufferZone is an easy one, and it largely remains unobtrusive. Yes, due to the fact it is essentially doubling the workload of running certain programs, it can all get a bit clogged up if used for extended periods. However, a quick wipe of the BufferZone soon sorts things out.
In fact, there are only really two reasons we can think of not to recommend this software and neither of them are technical issues. Rather, it’s all to do with our original question as to whether adding another string to your protection bow is worth it. You see, while BufferZone shields the delicate parts of your PC from a lot of malicious software run from web browsers or floppy disks, it can’t actually prevent a direct attack to your operating system from a remote source. To counter this you still need to keep up to date with OS patches and make sure you use a good hardware or software firewall. Likewise, if your system does become infected by some other means, BufferZone will never be able to tell, so you’ll still need a normal antivirus program to take care of that possibility.
So, if you don’t mind having yet another piece of, what is essentially, extraneous software to help keep your PC safe then we wholeheartedly recommend TrustWare’s BufferZone Pro – especially as you can trial it for 30-days free of charge. However, if all this software is getting a bit much we would advise you to maybe give this a miss and instead just mind where you browse and make sure you scan all software from external sources with your normal anti-virus before you run it. Oh, and always keep backups!
”’Verdict”’
TrustWare’s BufferZone is a brilliant new weapon in the constant battle to keep your PC free from malicious software. It may not replace any of your existing solutions but just like any good weapon, it plays its part and it plays it well. And, at around £15, for a single-user, time-unlimited license it is an absolute steal.

