HummingWhale malware plagues Android devices – what you need to know

Last year, security firm Check Point warned of a new type of Android malware called HummingBad, and now the company has issued yet another warning.
Originating from a well-organised group of Chinese developers going by the name of Yingmob, Hummingbad established a persistent rootkit on Android devices, generating fraudulent ad revenue and installing additional fraudulent apps.
These combined to generate around $300,000 per month in ad revenue for Yingmob, making Hummingbad a particularly lucrative malware enterprise.
Related: MWC 2017
Now, Check Point is warning of a new HummingBad variant called HummingWhale which it says has been hidden inside more than 20 Android apps and may have been downloaded millions of times.
The security firm said in an update: “This new variant, dubbed ‘HummingWhale,’ includes new, cutting edge techniques that allow it to perform ad fraud better than ever before.”
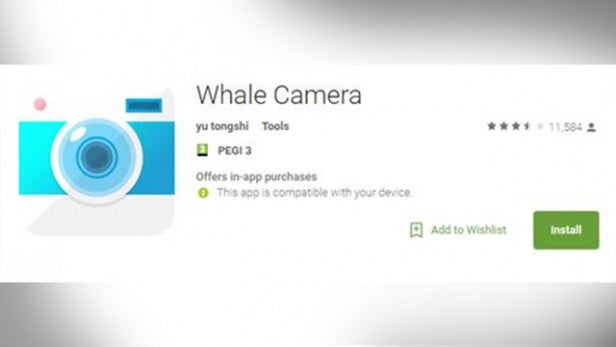
It added: “It was probably only a matter of time before HummingBad evolved and made its way onto Google Play.
“…HummingWhale malware first raised suspicions when Check Point researchers analyzed one of the apps.
“All of the apps were uploaded under the names of fake Chinese developers. In addition to the camera family, researchers were able to identify 16 additional, distinct package names related to the same malware, some of which were also found on Google Play.”
Check Point says it also identified several new HummingBad samples which promote the new HummingWhale version.
This is how the company says the malware works: “First, the Command and Control server (C&C) provides fake ads and apps to the installed malware, which presents them to the user.
“Once the user tries to close the ad, the app, which was already downloaded by the malware, is uploaded to the virtual machine and run as if it is a real device.
“This action generates the fake referrer id, which the malware uses to generate revenues for the perpetrators.”
But HummingWhale also conducts other malicious activities, including displaying illegitimate ads and hiding the original app after installation.
While Check Point doesn’t think the new version of the malware was produced by the same Yingmob group behind HummingBad, the company says whoever is behind HummingWhale seems to have learned from the previous version.
Google has already removed the HummingWhale apps from the Play Store according to the security firm’s update.
If you think you may have been infected, the best option is to simply carry out a factory reset of your device, after backing up any files such as photos and other media.
WATCH: What’s the no.1 smartphone in the world?
Let us know if you think you’ve been infected by HummingWhale in the comments.

