There’s a major new Android vulnerability that you need to know about

Android phones running versions of the operating system older than Android 8.0 Oreo could be at risk from a new vulnerability that allows malware to put fake overlays in front of users.
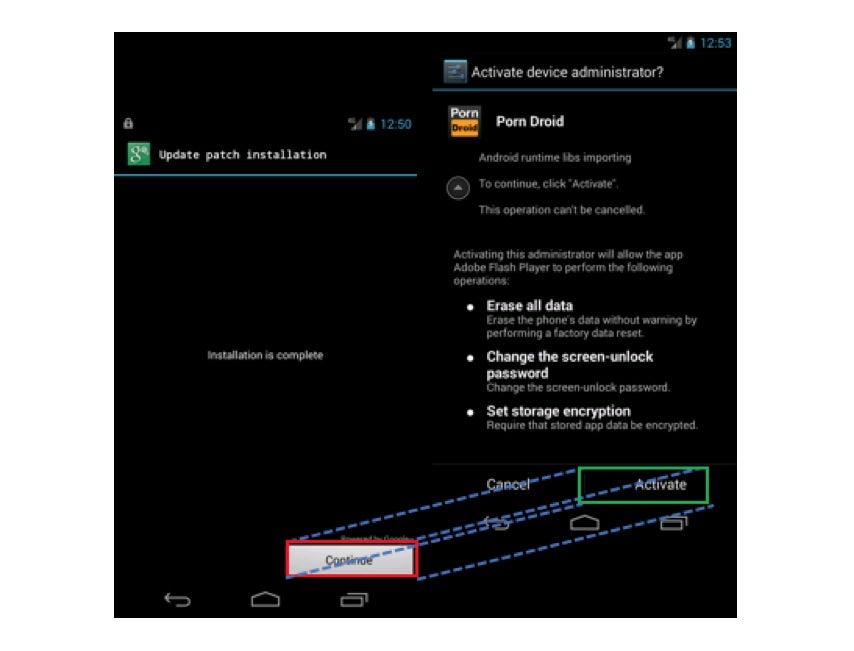
Discovered by cyber security firm Palo Alto Networks’ Unit 42 threat detection team, hackers can exploit a feature in older versions of Android called Toast, which allows apps to display pop up notifications, to draw fake app windows in Android that trick people into giving malware access to their device.
Once such malware has infected an Android phone or tablet it can lock up the OS and hold the phone’s software hostage in return for a ransom.
Normally, overlay attacks require Android users to give malicious apps direct explicit permission to draw overlay windows, and requires such apps to be installed from Google’s Play Store. These hurdles have meant that overlay cyber attacks haven’t really been something for people to worry about.
But the new vulnerability now allows malware to bypass those permissions and start causing problems.
 And those problems could be particularly nasty according to Christopher Budd, senior threat communications manager at Palo Alto Networks.
And those problems could be particularly nasty according to Christopher Budd, senior threat communications manager at Palo Alto Networks.
“What our researchers have found is a vulnerability that can be used to more easily enable an ‘overlay attack’, a type of attack that is already known on the Android platform. This type of attack is most likely to be used to get malicious software on the user’s Android device,” he explained.
“This type of attack can also be used to give malicious software total control over the device. In a worst-case attack scenario, this vulnerability could be used to render the phone unusable (i.e., a “brick”) or to install any kind of malware including (but not limited to) ransomware or information stealers.
“In simplest terms, this vulnerability could be used to take control of devices, lock devices and steal information after it is attacked.”
Android Oreo is immune to this this type of attack and the vulnerability thanks to the work Google has done on tightening up security on its mobile OS. But for users still waiting to have the latest version of Android pushed out to their phones, they are currently open to such attacks, so should be vary careful with the types of apps they download until Oreo is on their Android device.
Related: How to download Android Oreo
Have you been hit by an Android cyber attack? Let us know on Facebook or tweet @TrustedReviews.

