36 million Android devices could be infected with ‘Judy’ malware
Last week, security research firm Checkpoint identified a new type of Android malware that infected users’ devices with malicious ad-click software.
The malware was included in some apps available through the official Google Play Store, with Checkpoint saying between 8.5 and 36.5 million users could have been affected.
That means the malicious software could be the most wide-spread malware yet to hit the official Android app store.
At this time, the actual number of infected users remains unconfirmed, but Checkpoint warns the malware was present in some apps that had been available on the Play Store for “several years”.
Related: Best VPN
As the firm explains, the malware “is an auto-clicking adware which was found on 41 apps developed by a Korean company.”
Checkpoint says ‘Judy’ generates fraudulent clicks on ads, which results in revenue for the perpetrators, who created a “benign bridgehead app”, which inserts a connection to the users’ phone into the app store.
That means once a particular user downloads an app, it “silently registers receivers which establish a connection with the C&C server,” which in turn replies with the “malicious payload.”
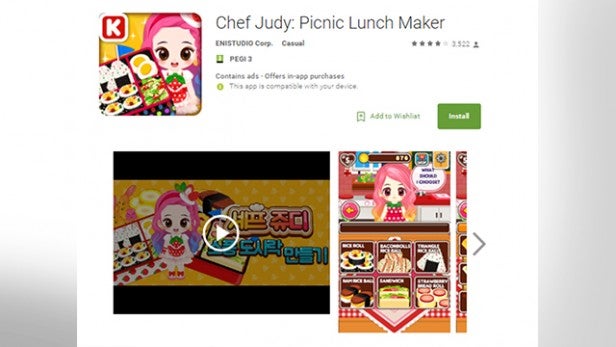
Google has reportedly removed the infected apps, which comprised several cooking and fashion games using the ‘Judy’ brand, from its Play Store after being notified by Checkpoint.
As the security firm explains: “The oldest app of the second campaign was last updated in April 2016, meaning that the malicious code hid for a long time on the Play store undetected.
“These apps also had a large amount of downloads between 4 and 18 million, meaning the total spread of the malware may have reached between 8.5 and 36.5 million users.”
The Korean publisher thought to be responsible for the infected apps is reportedly known as “ENISTUDIO,” though other publishers have also been said to have released apps with the malware included.
Precisely how the infected apps made it through the Google Play Store screening process remains unclear, but Checkpoint does offer the following explanation:
“Hackers can hide their apps’ real intentions or even manipulate users into leaving positive ratings, in some cases unknowingly.
“Users cannot rely on the official app stores for their safety, and should implement advanced security protections capable of detecting and blocking zero-day mobile malware.”
Let us know if you’ve been affected in the comments.

